Yotascale Security Guide
Overview
At Yotascale, security, confidentiality, integrity and availability of customer information and systems are our highest priority. We ensure this via a concerted and strategic combination of industry best practices, deep industry experience, and partnership with best-in-class providers such as Amazon Web Services (AWS). As a result, we have put an enormous amount of time and energy into robust security practices and continue to do so.
This document provides a high-level overview of this security posture.
Always encrypted data
Data is encrypted at all times and every step of the way; over the wire and at rest (RSA 2048 and SHA-256) using military grade encryption. All web connections are sent via 256-bit SSL.
We have put strong security measures in place to protect both your identity and access to your data. Strong and secure hash is used to store user passwords and immutable data such as session keys and certain account information. PBKDF2 along with HMAC is used for hash all such data along with a random salt for each user. Your AWS keys are encrypted using AWS 256 and then MAC for maximum security.
Secure AWS Account Access
Yotascale™ software uses roles for cross-account access which is the current best practice for granting access to resources in your AWS account to a trusted principal in a different account (Yotascale). Roles created to grant Yotascale software access to your account follow a specific policy that can easily be revoked by you at any time. Yotascale software always uses an external ID when assuming the cross-account role, according the AWS best practices.
AWS Partnership
Yotascale is an official solution provider and technology partner for Amazon Web Services.
Secure data centers
Yotascale software data is stored on AWS data centers that are ISO 27001 certification, PCI DSS Level 1 compliance, and SAS70 Type II. Learn more about AWS security.
Strict security and key management procedures
Staff members do not have the ability to decrypt encrypted account data, and we use extensive best practices to keep your sensitive information secure.
If you’d like more detail about our approach to security, we’d be happy to arrange a call with a member of your team. Email support@yotascale.com.
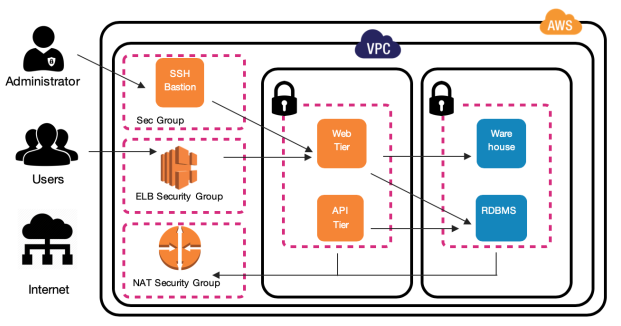
Yotascale Software High Level Architecture
Security Assessments & 3rd Party Audits
Yotascale understands and values the trust our customers place in us. We take security very seriously, and investigate all reported vulnerabilities. We are committed to yearly 3rd party vulnerability scans and mitigate all vulnerabilities found at the highest priority.
Yotascale employs the SAMM maturity model internally and enforces strict guidelines to follow security best practices throughout the entire organization. As part of the guidelines we are committed to regular (6 monthly) security audit and 3rd party penetration testing for all our our systems and have regularly passes these tests. Some of the best and most security aware companies are using our services.
We do not share any customer data with 3rd party or vendors.
Data Retention
Yotascale removes all customer data 30 days after their contract expires.
If you would like to report a vulnerability, you may do so by submitting a report to security@yotascale.com including a demonstrable example of the vulnerability.
